This chapter provides an overview of the TCP/IP protocol suite,
to establish an adequate background for the remaining chapters.
For a historical perspective on the early development of TCP/IP
see [Lynch 1993].
1.2 Layering
Networking protocols are normally developed in layers,
with each layer responsible for a different facet of the communications.
A protocol suite, such as TCP/IP, is the combination of
different protocols at various layers. TCP/IP is normally considered
to be a 4-layer system, as shown in Figure 1.1.
| Telnet, FTP, e-mail, etc. | |
| TCP, UDP | |
| IP, ICMP, IGMP | |
| device driver and interface card |
Each layer has a different responsibility.
TCP provides a reliable flow of data between two hosts. It is concerned with things such as dividing the data passed to it from the application into appropriately sized chunks for the network layer below, acknowledging received packets, setting timeouts to make certain the other end acknowledges packets that are sent, and so on. Because this reliable flow of data is provided by the transport layer, the application layer can ignore all these details.
UDP, on the other hand, provides a much simpler service to the application layer. It just sends packets of data called datagrams from one host to the other, but there is no guarantee that the datagrams reach the other end. Any desired reliability must be added by the application layer.
There is a use for each type of transport protocol, which we'll see when we look at the different applications that use TCP and UDP.
and many more, some of which we cover in later chapters.
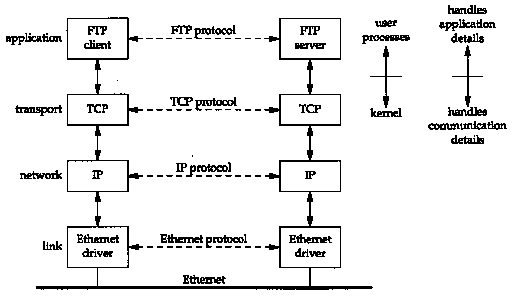
If we have two hosts on a local area network (LAN) such as an Ethernet, both running FTP, Figure 1.2 shows the protocols involved.

We have labeled one application box the FTP client and the other the FTP server. Most network applications are designed so that one end is the client and the other side the server. The server provides some type of service to clients, in this case access to files on the server host. In the remote login application, Telnet, the service provided to the client is the ability to login to the server's host.
Each layer has one or more protocols for communicating with its peer at the same layer. One protocol, for example, allows the two TCP layers to communicate, and another protocol lets the two IP layers communicate.
On the right side of Figure 1.2 we have noted that normally the application layer is a user process while the lower three layers are usually implemented in the kernel (the operating system). Although this isn't a requirement, it's typical and this is the way it's done under Unix.
There is another critical difference between the top layer in Figure 1.2 and the lower three layers. The application layer is concerned with the details of the application and not with the movement of data across the network. The lower three layers know nothing about the application but handle all the communication details.
We show four protocols in Figure 1.2, each at a different layer. FTP is an application layer protocol, TCP is a transport layer protocol, IP is a network layer protocol, and the Ethernet protocols operate at the link layer. The TCP/IP protocol suite is a combination of many protocols. Although the commonly used name for the entire protocol suite is TCP/IP, TCP and IP are only two of the protocols. (An alternative name is the Internet Protocol Suite.)
The purpose of the network interface layer and the application layer are obvious-the former handles the details of the communication media (Ethernet, token ring, etc.) while the latter handles one specific user application (FTP, Telnet, etc.). But on first glance the difference between the network layer and the transport layer is somewhat hazy. Why is there a distinction between the two? To understand the reason, we have to expand our perspective from a single network to a collection of networks.
One of the reasons for the phenomenal growth in networking during the 1980s was the realization that an island consisting of a stand-alone computer made little sense. A few stand-alone systems were collected together into a network. While this was progress, during the 1990s we have come to realize that this new, bigger island consisting of a single network doesn't make sense either. People are combining multiple networks together into an internetwork, or an internet. An internet is a collection of networks that all use the same protocol suite.
The easiest way to build an internet is to connect two or more networks with a router. This is often a special-purpose hardware box for connecting networks. The nice thing about routers is that they provide connections to many different types of physical networks: Ethernet, token ring, point-to-point links, FDDI (Fiber Distributed Data Interface), and so on.
These boxes are also called IP routers, but
we'll use the term router.
Historically these boxes were called gateways,
and this term is used throughout much of the TCP/IP literature.
Today the term gateway is used for an application gateway:
a process that connects two different protocol suites (say, TCP/IP
and IBM's SNA) for one particular application (often electronic
mail or file transfer).
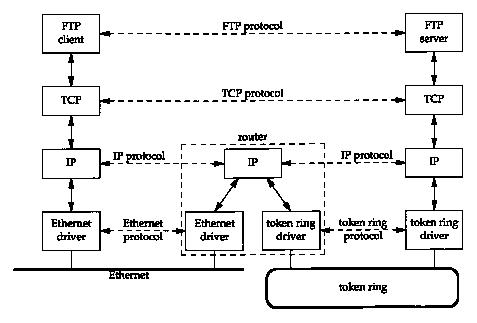
Figure 1.3 shows an internet consisting of two networks: an Ethernet and a token ring, connected with a router. Although we show only two hosts communicating, with the router connecting the two networks, any host on the Ethernet can communicate with any host on the token ring.
In Figure 1.3 we can differentiate between an end system (the two hosts on either side) and an intermediate system (the router in the middle). The application layer and the transport layer use end-to-end protocols. In our picture these two layers are needed only on the end systems. The network layer, however, provides a hop-by-hop protocol and is used on the two end systems and every intermediate system.
In the TCP/IP protocol suite the network layer, IP, provides an unreliable service. That is, it does its best job of moving a packet from its source to its final destination, but there are no guarantees. TCP, on the other hand, provides a reliable transport layer using the unreliable service of IP To provide this service, TCP performs timeout and retransmission, sends and receives end-to-end acknowledgments, and so on. The transport layer and the network layer have distinct responsibilities.
A router, by definition, has two or more network interface layers (since it connects two or more networks). Any system with multiple interfaces is called multihomed. A host can also be multihomed but unless it specifically forwards packets from one interface to another, it is not called a router. Also, routers need not be special hardware boxes that only move packets around an internet. Most TCP/IP implementations allow a multihomed host to act as a router also, but the host needs to be specifically configured for this to happen. In this case we can call the system either a host (when an application such as FTP or Telnet is being used) or a router (when it's forwarding packets from one network to another). We'll use whichever term makes sense given the context.
One of the goals of an internet is to hide all the details of the physical layout of the internet from the applications. Although this isn't obvious from our two-network internet in Figure 1.3, the application layers can't care (and don't care) that one host is on an Ethernet, the other on a token ring, with a router between. There could be 20 routers between, with additional types of physical interconnections, and the applications would run the same. This hiding of the details is what makes the concept of an internet so powerful and useful.
Another way to connect networks is with a bridge. These connect networks at the link layer, while routers connect networks at the network layer. Bridges makes multiple LANs appear to the upper layers as a single LAN.
TCP/IP internets tend to be built using routers instead of bridges,
so we'll focus on routers. Chapter 12 of [Perlman
1992] compares routers and bridges.
1.3 TCP/IP Layering
There are more protocols in the TCP/IP protocol suite. Figure
1.4 shows some of the additional protocols that we talk about
in this text.
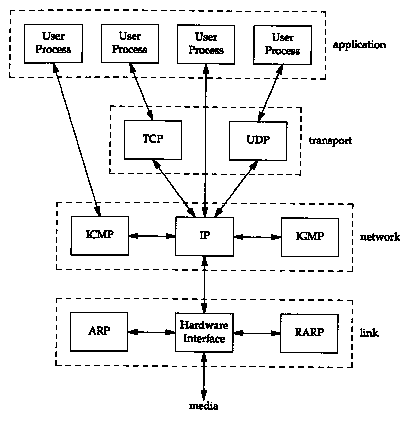
TCP and UDP are the two predominant transport layer protocols. Both use IP as the network layer.
TCP provides a reliable transport layer, even though the service it uses (IP) is unreliable. Chapters 17 through 22 provide a detailed look at the operation of TCP. We then look at some TCP applications: Telnet and Riogin in Chapter 26, FTP in Chapter 27, and SMTP in Chapter 28. The applications are normally user processes.
UDP sends and receives datagrams for applications. A datagram is a unit of information (i.e., a certain number of bytes of information that is specified by the sender) that travels from the sender to the receiver. Unlike TCP, however, UDP is unreliable. There is no guarantee that the datagram ever gets to its final destination. Chapter 11 looks at UDP, and then Chapter 14 (the Domain Name System), Chapter 15 (the Trivial File Transfer Protocol), and Chapter 16 (the Bootstrap Protocol) look at some applications that use UDP. SNMP (the Simple Network Management Protocol) also uses UDP, but since it deals with many of the other protocols, we save a discussion of it until Chapter 25.
IP is the main protocol at the network layer. It is used by both TCP and UDP. Every piece of TCP and UDP data that gets transferred around an internet goes through the IP layer at both end systems and at every intermediate router. In Figure 1.4 we also show an application accessing IP directly. This is rare, but possible. (Some older routing protocols were implemented this way. Also, it is possible to experiment with new transport layer protocols using this feature.) Chapter 3 looks at IP, but we save some of the details for later chapters where their discussion makes more sense. Chapters 9 and 10 look at how IP performs routing.
ICMP is an adjunct to IP. It is used by the IP layer to exchange error messages and other vital information with the IP layer in another host or router. Chapter 6 looks at ICMP in more detail. Although ICMP is used primarily by IP, it is possible for an application to also access it. Indeed we'll see that two popular diagnostic tools, Ping and Traceroute (Chapters 7 and 8), both use ICMP.
IGMP is the Internet Group Management Protocol. It is used with multicasting: sending a UDP datagram to multiple hosts. We describe the general properties of broadcasting (sending a UDP datagram to every host on a specified network) and multicasting in Chapter 12, and then describe IGMP itself in Chapter 13.
ARP (Address Resolution Protocol)
and RARP (Reverse Address Resolution
Protocol) are specialized protocols used only with certain types
of network interfaces (such as Ethernet and token ring) to convert
between the addresses used by the IP layer and the addresses used
by the network interface. We examine these protocols in
Chapters 4 and 5, respectively.
1.4 Internet Addresses
Every interface on an internet must have a unique Internet
address (also called an IP address). These addresses
are 32-bit numbers. Instead of using a flat address space such
as 1, 2, 3, and so on, there is a structure to Internet addresses.
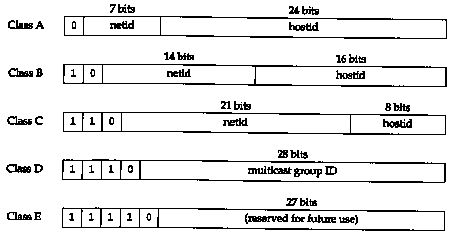
Figure 1.5 shows the five different classes of Internet addresses.
These 32-bit addresses are normally written as four decimal numbers, one for each byte of the address. This is called dotted-decimal notation. For example, the class B address of the author's primary system is 140.252.13.33.
The easiest way to differentiate between the different classes of addresses is to look at the first number of a dotted-decimal address. Figure 1.6 shows the different classes, with the first number in boldface.
| 0.0.0.0 to 127.255.255.255 | |
| 128.0.0.0 to 191.255.255.255 | |
| 192.0.0.0 to 223.255.255.255 | |
| 224.0.0.0 to 239.255.255.255 | |
| 240.0.0.0 to 247.255.255.255 |
It is worth reiterating that a multihomed host will have multiple IP addresses: one per interface.
Since every interface on an internet must have a unique IP address, there must be one central authority for allocating these addresses for networks connected to the worldwide Internet. That authority is the Internet Network Information Center, called the InterNIC. The InterNIC assigns only network IDs. The assignment of host IDs is up to the system administrator.
Registration services for the Internet (IP addresses and DNS
domain names) used to be handled by the NIC,
at nic.ddn.mil.
On April 1, 1993, the InterNIC was created. Now the NIC
handles these requests only for the Defense Data Network
(DDN). All other Internet users now use the InterNIC registration
services, at rs.internic.net.
There are actually three parts to the InterNIC:
registration services (rs.internic.net),
directory and database services (ds.internic.net),
and information services (is.internic.net).
See Exercise 1.8 for additional information on the InterNIC.
There are three types of IP addresses: unicast (destined for a single host), broadcast (destined for all hosts on a given network), and multicast (destined for a set of hosts that belong to a multicast group). Chapters 12 and 13 look at broadcasting and multicasting in more detail.
In Section 3.4 we'll extend our description of IP addresses to
include subnetting, after describing IP routing. Figure 3.9 shows
the special case IP addresses: host IDs
and network IDs of all zero bits or all one bits.
1.5 The Domain Name System
Although the network interfaces on a host, and therefore the host
itself, are known by IP addresses, humans work best using
the name of a host. In the TCP/IP world the Domain Name
System (DNS) is a distributed
database that provides the mapping between IP addresses and hostnames.
Chapter 14 looks into the DNS in detail.
For now we must be aware that any application can call a standard library function to look up the IP address (or addresses) corresponding to a given hostname. Similarly a function is provided to do the reverse lookup-given an IP address, look up the corresponding hostname.
Most applications that take a hostname as an argument also take
an IP address. When we use the Telnet
client in Chapter 4, for example, one time we specify a host-name
and another time we specify an IP address.
1.6 Encapsulation
When an application sends data using TCP, the data is sent down
the protocol stack, through each layer, until it is sent as a
stream of bits across the network. Each layer adds information
to the data by prepending headers (and sometimes adding trailer
information) to the data that it receives. Figure 1.7 shows this
process. The unit of data that TCP sends to IP is called a TCP
segment. The unit of data that IP sends to the network interface
is called an IP datagram. The stream of bits that flows
across the Ethernet is called a frame.
The numbers at the bottom of the headers and trailer of the Ethernet frame in Figure 1.7 are the typical sizes of the headers in bytes. We'll have more to say about each of these headers in later sections.
A physical property of an Ethernet frame is that the size of its data must be between 46 and 1500 bytes. We'll encounter this minimum in Section 4.5 and we cover the maximum in Section 2.8.
All the Internet standards
and most books on TCP/IP use the term octet instead of
byte. The use of this cute, but baroque term is historical, since
much of the early work on TCP/IP was done on systems such as the
DEC-10, which did not use 8-bit bytes. Since almost every current
computer system uses 8-bit bytes, we'll use the term byte
in this text.
To be completely accurate in Figure 1.7 we should
say that the unit of data passed between IP and the network interface
is a packet. This packet can be either an IP datagram or
a fragment of an IP datagram. We discuss fragmentation in detail
in Section 11.5.
We could draw a nearly identical picture for UDP data. The only changes are that the unit of information that UDP passes to IP is called a UDP datagram, and the size of the UDP header is 8 bytes.
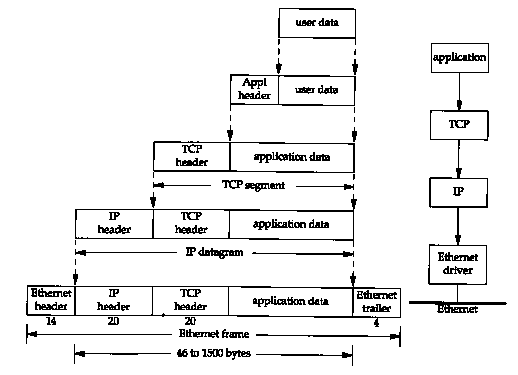
Recall from Figure 1.4 that TCP, UDP, ICMP, and IGMP all send data to IP. IP must add some type of identifier to the IP header that it generates, to indicate the layer to which the data belongs. IP handles this by storing an 8-bit value in its header called the protocol field. A value of 1 is for ICMP, 2 is for IGMP, 6 indicates TCP, and 17 is for UDP.
Similarly, many different applications can be using TCP or UDP at any one time. The transport layer protocols store an identifier in the headers they generate to identify the application. Both TCP and UDP use 16-bit port numbers to identify applications. TCP and UDP store the source port number and the destination port number in their respective headers.
The network interface sends and receives frames on behalf of IP,
ARP, and RARP.
There must be some form of identification in the Ethernet
header indicating which network layer protocol generated the data.
To handle this there is a 16-bit frame type field in the Ethernet
header.
1.7 Demultiplexing
When an Ethernet frame is received at the destination host it
starts its way up the protocol stack and all the headers are removed
by the appropriate protocol box. Each protocol box looks at certain
identifiers in its header to determine which box in the next upper
layer receives the data. This is called demultiplexing.
Figure 1.8 shows how this takes place.
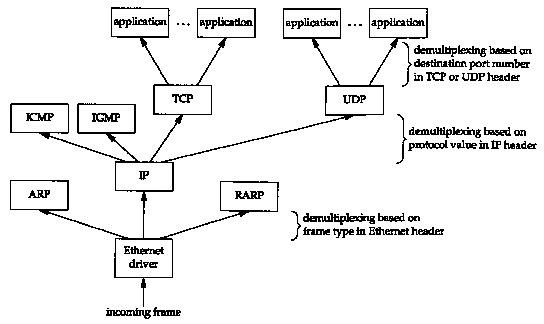
Positioning the protocol boxes labeled "ICMP"
and "IGMP" is always a
challenge. In Figure 1.4 we showed them at the same layer as IP,
because they really are adjuncts to IP. But here we show them
above IP, to reiterate that ICMP messages and IGMP messages are
encapsulated in IP datagrams.
We have a similar problem with the boxes "ARP"
and "RARP." Here we show
them above the Ethernet device driver because they both have their
own Ethernet frame types, like IP datagrams. But in Figure 2.4
we'll show ARP as part of the Ethernet device driver, beneath
IP, because that's where it logically fits.
Realize that these pictures of layered protocol boxes are not
perfect.
When we describe TCP in detail we'll see that it really demultiplexes
incoming segments using the destination port number, the source
IP address, and the source port number.
1.8 Client-Server Model
Most networking applications are written assuming one side is
the client and the other the server. The purpose of the application
is for the server to provide some defined service for clients.
We can categorize servers into two classes: iterative or concurrent. An iterative server iterates through the following steps.
I1. Wait for a client request to arrive.
I2. Process the client request.
I3. Send the response back to the client that sent the request.
I4. Go back to step I1.
The problem with an iterative server is when step I2 takes a while. During this time no other clients are serviced. A concurrent server, on the other hand, performs the following steps.
Cl. Wait for a client request to arrive.
C2. Start a new server to handle this client's request. This may involve creating a new process, task, or thread, depending on what the underlying operating system supports. How this step is performed depends on the operating system.
This new server handles this client's entire request. When complete, this new server terminates.
C3. Go back to step Cl.
The advantage of a concurrent server is that the server just spawns other servers to handle the client requests. Each client has, in essence, its own server. Assuming the operating system allows multiprogramming, multiple clients are serviced concurrently.
The reason we categorize servers, and not clients, is because a client normally can't tell whether it's talking to an iterative server or a concurrent server.
As a general rule, TCP servers are concurrent, and UDP
servers are iterative, but there are a few exceptions. We'll look
in detail at the impact of UDP on its servers in Section 11.12,
and the impact of TCP on its servers in Section 18.11.
1.9 Port Numbers
We said that TCP and UDP identify applications using 16-bit port
numbers. How are these port numbers chosen?
Servers are normally known by their well-known port number. For example, every TCP/IP implementation that provides an FTP server provides that service on TCP port 21. Every Telnet server is on TCP port 23. Every implementation of TFTP (the Trivial File Transfer Protocol) is on UDP port 69. Those services that can be provided by any implementation of TCP/IP have well-known port numbers between 1 and 1023. The well-known ports are managed by the Internet Assigned Numbers Authority (IANA).
Until 1992 the well-known ports were between I and
255. Ports between 256 and 1023 were normally used by Unix systems
for Unix-specific services-that is, services found on a Unix system,
but probably not found on other operating systems. The IANA now
manages the ports between 1 and 1023.
An example of the difference between an Internet-wide
service and a Unix-specific service is the difference between
Telnet and Riogin. Both allow us
to login across a network to another host. Telnet is a TCP/IP
standard with a well-known port number of 23 and can be implemented
on almost any operating system. Rlogin,
on the other hand, was originally designed for Unix systems (although
many non-Unix systems now provide it also) so its well-known port
was chosen in the early 1980s as 513.
A client usually doesn't care what port number it uses on its end. All it needs to be certain of is that whatever port number it uses be unique on its host. Client port numbers are called ephemeral ports (i.e., short lived). This is because a client typically exists only as long as the user running the client needs its service, while servers typically run as long as the host is up.
Most TCP/IP implementations allocate ephemeral port numbers between 1024 and 5000. The port numbers above 5000 are intended for other servers (those that aren't well known across the Internet). We'll see many examples of how ephemeral ports are allocated in the examples throughout the text.
Solaris 2.2 is a notable exception. By default the ephemeral ports for TCP and UDP start at 32768. Section E.4 details the configuration options that can be modified by the system administrator to change these defaults.
The well-known port numbers are contained in the file /etc/services on most Unix systems. To find the port numbers for the Telnet server and the Domain Name System, we can execute
| sun % grep telnet /etc/services
telnet 23/tcp | says it uses TCP port 23 |
| sun % grep domain /etc/services domain 53/udp domain 53/tcp | says it uses UDP port 53
and TCP port 53 |
These port numbers are in the range of 1 to 1023, and are used
by some applications (notably Rlogin,
Section 26.2), as part of the authentication between the client
and server.
1.10 Standardization Process
Who controls the TCP/IP protocol suite, approves new standards,
and the like? There are four groups responsible for Internet technology.
Both the IRTF and the IETF fall under the IAB. [Crocker
1993] provides additional details on the standardization process
within the Internet, as well as
some of its early history.
1.11 RFCs
All the official standards in the internet community are published
as a Request for Comment, or RFC.
Additionally there are lots of RFCs that are not official standards,
but are published for informational purposes. The RFCs range in
size from I page to almost 200 pages. Each is identified by a
number, such as RFC 1122, with higher numbers for newer RFCs.
All the RFCs are available at no charge through electronic mail or using FTP across the Internet. Sending electronic mail as shown here:
| To: rfc-info@OISI.EDU
Subject: getting rfcs help: ways_to_get_rfcs |
returns a detailed listing of various ways to obtain the RFCs.
The latest RFC index is always a starting point when looking for something. This index specifies when a certain RFC has been replaced by a newer RFC, and if a newer RFC updates some of the information in that RFC. There are a few important RFCs.
When this RFC is updated (it is normally updated at least yearly) the index listing for 1340 will indicate which RFC has replaced it.
Like the Assigned Numbers RFC, this RFC is also reissued regularly. Be sure you're reading the current copy.
[Borman 1993b] provides a practical look at these two RFCs, and RFC 1127 [Braden 1989c] provides an informal summary of the discussions and conclusions of the working group that developed the Host Requirements RFCs.
If we examine the port numbers for these standard services and other standard TCP/IP services (Telnet, FTP, SMTP, etc.), most are odd numbers. This is historical as these port numbers are derived from the NCP port numbers. (NCP, the Network Control Protocol, preceded TCP as a transport layer protocol for the ARPANET.) NCP was simplex, not full-duplex, so each application required two connections, and an even-odd pair of port numbers was reserved for each application. When TCP and UDP became the standard transport layers, only a single port number was needed per application, so the odd port numbers from NCP were used.
| Name | Description | |||
| echo | Server returns whatever the client sends. | |||
| discard | Server discards whatever the client sends. | |||
| daytime | Server returns the time and date in a human-readable format. | |||
| chargen | TCP server sends a continual stream of characters, until the connection is terminated by the client. UDP server sends a datagram containing a random number of characters each time the client sends a datagram. | |||
| time | Server returns the time as a 32-bit binary number. This number represents the number of seconds since midnight January 1, 1900, UTC. |
The lowercase internet means multiple networks connected
together, using a common protocol suite. The uppercase Internet
refers to the collection of hosts (over one million) around the
world that can communicate with each other using TCP/IP. While
the Internet is an internet, the reverse is not true.
1.14 Implementations
The de facto
standard for TCP/IP implementations is the one from the Computer
Systems Research Group at the University of California
at Berkeley. Historically this has been distributed with the 4.x
BSD system (Berkeley Software Distribution),
and with the "BSD Networking
Releases." This source code has been the starting point for
many other implementations.
Figure 1.10 shows a chronology of the various BSD releases, indicating the important TCP/IP features. The BSD Networking Releases shown on the left side are publicly available source code releases containing all of the networking code: both the protocols themselves and many of the applications and utilities (such as Telnet and FTP).
Throughout the text we'll use the term Berkeley-derived implementation to refer to vendor implementations such as SunOS 4.x, SVR4, and AIX 3.2 that were originally developed from the Berkeley sources. These implementations have much in common, often including the same bugs!
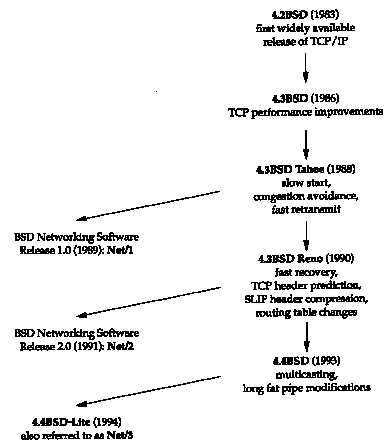
Much of the original research in the Internet
is still being applied to the Berkeley system-new congestion control
algorithms (Section 21.7), multicasting
(Section 12.4), "long
fat pipe" modifications (Section 24.3), and the like.
1.15 Application Programming Interfaces
Two popular application programming
interfaces (APIs) for applications using the TCP/IP protocols
are called sockets and TLI
(Transport Layer Interface). The former is sometimes called "Berkeley
sockets," indicating where it was originally developed. The
latter, originally developed by AT&T, is sometimes called
XTI (X/Open
Transport Interface), recognizing the work done by X/Open, an
international group of computer vendors that produce their own
set of standards. XTI is effectively a superset of TLI.
This text is not a programming text, but occasional reference
is made to features of TCP/IP that we look at, and whether that
feature is provided by the most popular API (sockets) or not.
All the programming details for both sockets and TLI
are available in [Stevens 1990].
1.16 Test Network
Figure 1.11 shows the test network that is used for all the examples
in the text. This figure is also duplicated on the inside front
cover for easy reference while reading the book.
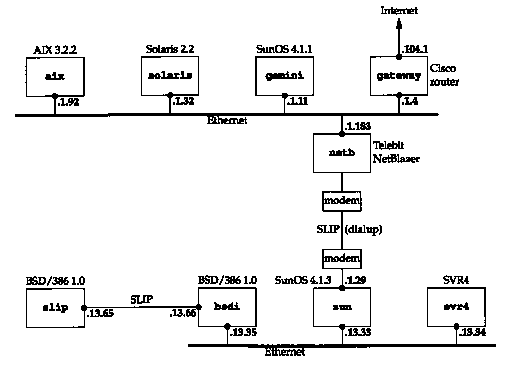
Most of the examples are run on the lower four systems in this figure (the author's subnet). All the IP addresses in this figure belong to the class B network ID 140.252. All the hostnames belong to the .tuc.noao.edu domain.(noao stands for "National Optical Astronomy Observatories" and tuc stands for Tucson.) For example, the lower right system has a complete hostname of svr4.tuc.noao.edu and an IP address of 140.252.13.34. The notation at the top of each box is the operating system running on that system. This collection of systems and networks provides hosts and routers running a variety of TCP/IP implementations.
It should be noted that there are many more networks and hosts in the noao.edu domain than we show in Figure 1.11. All we show here are the systems that we'll encounter throughout the text.
In Section 3.4 we describe the form of subnetting used on this
network, and in Section 4.6 we'll provide more details on the
dial-up SLIP connection between
sun and netb.
Section 2.4 describes SLIP in detail.
1.17 Summary
This chapter has been a whirlwind tour of the TCP/IP protocol
suite, introducing many of the terms and protocols that we discuss
in detail in later chapters.
The four layers in the TCP/IP protocol suite are the link layer, network layer, transport layer, and application layer, and we mentioned the different responsibilities of each. In TCP/IP the distinction between the network layer and the transport layer is critical: the network layer (IP) provides a hop-by-hop service while the transport layers (TCP and UDP) provide an end-to-end service.
An internet is a collection of networks. The common building block for an internet is a router that connects the networks at the IP layer. The capital-l Internet is an internet that spans the globe and consists of more than 10,000 networks and more than one million computers.
On an internet each interface is identified by a unique IP address, although users tend to use hostnames instead of IP addresses. The Domain Name System provides a dynamic mapping between hostnames and IP addresses. Port numbers are used to identify the applications communicating with each other and we said that servers use well-known ports while clients use ephemeral ports.
1.2 Fetch the file nsfnet/statistics/history.netcount using anonymous FTP (Section 27.3) from the host nic.merit.edu. This file contains the number of domestic and foreign networks announced to the NSFNET infrastructure. Plot these values with the year on the x-axis and a logarithmic y-axis with the total number of networks. The maximum value for the y-axis should be the value calculated in the previous exercise. If the data shows a visual trend, extrapolate the values to estimate when the current addressing scheme will run out of network IDs. (Section 3.10 talks about proposals to correct this problem.)
1.3 Obtain a copy of the Host Requirements RFC [Braden 1989a] and look up the robustness principle that applies to every layer of the TCP/IP protocol suite. What is the reference for this principle?
1.4 Obtain a copy of the latest Assigned Numbers RFC. What is the well-known port for the "quote of the day" protocol? Which RFC defines the protocol?
1.5 If you have an account on a host that is connected to a TCP/IP internet, what is its primary IP address? Is the host connected to the worldwide Internet? Is it multihomed?
1.6 Obtain a copy of RFC 1000 to learn where the term RFC originated.
1.7 Contact the Internet Society, isoc@isoc.org or +1 703 648 9888, to find out about joining.
1.8 Fetch the fileabout-internic/information-about-the-internic using anonymous FTP from the host is.internic.net.